Table of Contents
Accounts Payable (AP) fraud represents a significant threat to businesses of all sizes, potentially causing devastating financial losses and reputational damage. This form of financial malfeasance involves the manipulation of an organization's payment processes for personal gain. According to the Association of Certified Fraud Examiners' 2024 Report to the Nations, the median loss from a single case of AP fraud is a staggering $145,000 with some cases resulting in multimillion-dollar losses.
As businesses increasingly rely on digital payment systems, the landscape of AP fraud continues to evolve, presenting new challenges for financial professionals and business owners alike. Understanding the various types of AP fraud, recognizing red flags, and implementing robust prevention strategies are crucial steps in safeguarding your organization's financial integrity.
What are the Most Common Types of Accounts Payable Fraud?
Accounts Payable (AP) fraud comes in various forms, each with its own set of challenges and red flags. Understanding these common types of fraud is crucial for businesses to protect their financial assets. Let's delve into the five most prevalent forms of AP fraud, exploring their characteristics, common scenarios, and typical perpetrators.
1. Billing Schemes
Billing schemes are perhaps the most common type of AP fraud. In these schemes, fraudsters manipulate the billing system to siphon money from the company. This can occur in several ways:
- Fictitious Vendors: A fraudster creates a fake vendor account and submits false invoices for payment.
- Shell Companies: Similar to fictitious vendors, but involving the creation of a real business entity that exists solely to facilitate fraud.
- Personal Purchases: An employee uses company funds to pay for personal items, a way disguising them as legitimate business expenses.
Impact on Businesses:
Billing schemes can have severe consequences for organizations, including:
- Direct financial losses, often accumulating over time
- Increased costs of goods or services due to inflated invoices
- Damaged relationships with legitimate vendors due to payment discrepancies
- Potential legal and regulatory issues if fraudulent activity is not caught and reported
- Erosion of investor and stakeholder confidence if the fraud becomes public
Common scenarios include an accounts payable clerk setting up a fictitious vendor that they control, or a purchasing manager creating a shell company to invoice for non-existent goods or services.
Perpetrators are often employees with access to the vendor management system and the ability to approve new vendors or invoices. In some cases, collusion between an employee and an external party may occur.
2. Check Tampering
Check tampering involves the interception and alteration of legitimate checks or the creation of unauthorized checks. This fraud type includes:
- Forged Maker Schemes: Creating entirely fake checks or forging signatures on legitimate checks.
- Forged Endorsement Schemes: Intercepting checks intended for legitimate payees and endorsing them for personal use.
- Altered Payee Schemes: Modifying the payee name on a legitimate check.
Impact on Businesses:
Check tampering can lead to significant issues for businesses that include
- Immediate financial losses from fraudulent check cashing
- Bank fees and penalties for overdrafts or insufficient funds
- Time and resources spent investigating discrepancies and resolving issues with banks
- Potential damage to credit rating if checks bounce due to fraud
- Loss of control over cash flow management
A common scenario might involve an accounts payable employee intercepting an outgoing check, altering the payee name, and depositing it into their personal account.
Perpetrators are typically employees with access to check stock, signature stamps, or the ability to intercept outgoing mail. This could include accounts payable staff, mailroom employees, or even executives with check-signing authority.
3. ACH (Automated Clearing House) Fraud
As businesses increasingly move towards electronic payments, ACH fraud has become more prevalent. This type of fraud involves:
- Unauthorized ACH Transfers: Initiating electronic transfers without proper authorization.
- Manipulation of ACH Payment Details: Altering recipient bank details to divert funds.
Impact on Businesses:
ACH fraud can have far-reaching consequences that include
- Large-scale financial losses due to the speed and volume of electronic transfers
- Disruption of relationships with vendors due to misdirected payments
- Increased cybersecurity costs to prevent and detect fraudulent activities
- Potential regulatory fines for inadequate security measures
- Loss of trust in electronic payment systems, potentially slowing down business operations
A typical scenario might involve a finance employee changing the bank account details for a legitimate vendor to their own account number, then initiating an ACH transfer.
Perpetrators are usually employees with access to the company's banking systems and ACH transfer capabilities. This could include treasury staff, accounts payable clerks, or IT personnel with back-end access to financial systems.
4. Expense Reimbursement Fraud
Expense reimbursement fraud occurs when employees manipulate the expense reporting process for personal gain. This can manifest as:
- Mischaracterized Expenses: Claiming personal expenses as business-related.
- Overstated Expenses: Inflating the cost of legitimate business expenses.
- Fictitious Expenses: Submitting claims for expenses that never occurred.
Impact on Businesses
Expense reimbursement fraud can affect businesses in various ways which includes
- Cumulative financial losses that can be significant over time
- Inflated operational costs leading to reduced profitability
- Decreased employee morale if fraudulent behavior is perceived to go unchecked
- Time and resources spent on increased oversight and auditing of expense reports
- Potential tax implications if fraudulent expenses are claimed as business deductions
A common scenario might involve a salesperson claiming inflated mileage for business trips or submitting receipts for meals that never took place.
Perpetrators can be employees at any level who submit expense reports, but it's particularly common among those who travel frequently or entertain clients, such as sales staff or executives.
5. Kickback Schemes
Kickback schemes involve collusion between an employee and an external vendor. The employee facilitates payments to the vendor in exchange for a portion of the profits. This can include:
- Vendor Collusion: An employee approves inflated invoices from a vendor in exchange for a percentage of the overpayment.
- Employee-Vendor Conspiracies: An employee and vendor work together to create entirely fictitious transactions.
A typical scenario might involve a procurement manager consistently selecting a particular vendor for contracts, with that vendor providing personal payments or gifts in return.
Perpetrators usually include employees with purchasing power or influence over vendor selection, such as procurement managers, project managers, or executives. The scheme also involves corrupt vendors willing to participate in fraudulent activities.
Understanding these common types of AP fraud is the first step in prevention. By recognizing the characteristics, scenarios, and typical perpetrators associated with each type, businesses can implement targeted controls and detection mechanisms to safeguard their financial resources.
6. Document Fraud
Document fraud in Accounts Payable involves the manipulation, fabrication, or alteration of documents used in the payment process. This can include:
- Invoice Manipulation: Altering legitimate invoices to inflate amounts or change payment details.
- Forged Approvals: Creating fake approval signatures or stamps on fraudulent documents.
- Duplicate Invoicing: Submitting the same invoice multiple times for payment.
- Altered Purchase Orders: Modifying purchase orders to justify fraudulent payments.
Impact on Businesses
Kickback schemes can have serious repercussions including
- Inflated costs for goods and services, reducing overall profitability
- Compromised quality of products or services due to vendor selection based on kickbacks rather than merit
- Legal and regulatory risks, including potential violations of anti-bribery laws
- Damage to company reputation if schemes become public
- Erosion of ethical culture within the organization
A common scenario might involve an accounts payable clerk creating a fake invoice that closely resembles a legitimate vendor's invoice but with altered payment details. Another scenario could be a manager forging approval signatures on fraudulent expense reports. Perpetrators of document fraud can be found at various levels within an organization. They often include:
- Accounts payable staff with access to incoming invoices and the ability to enter them into the system.
- Managers or executives who can approve documents without close scrutiny.
- Employees in positions that allow them to create or modify official documents, such as purchase orders or contracts.
- In some cases, external parties like vendors might collude with internal employees to create and submit fraudulent documents.
Document fraud can be particularly challenging to detect because it often involves the manipulation of seemingly legitimate paperwork. This type of fraud exploits the trust placed in official documents and can bypass controls that rely on proper documentation.
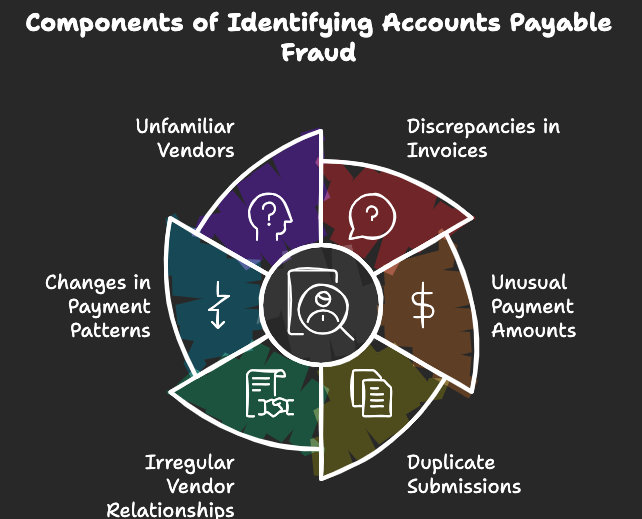
How to Spot Accounts Payable Fraud in your Organization
Detecting Accounts Payable (AP) fraud early can save your organization from significant financial losses and reputational damage. While fraudsters are continually developing new methods to evade detection, there are several red flags and techniques that can help you identify potential fraud. These include:
1. Unusual Vendor Activity
One of the primary indicators of AP fraud is abnormal vendor behavior or suspicious new vendors.
Key indicators to watch for:
- Sudden increase in invoices from a particular vendor
- New vendors with vague or generic company names
- Vendor addresses matching employee addresses or P.O. boxes
- Vendors with only a phone number or email for contact
How to monitor:
- Regularly review the vendor master file for duplicates or suspicious entries
- Implement a thorough vendor vetting process for all new vendors
- Use data analytics to identify unusual patterns in vendor invoicing or payments
Vigilance in monitoring vendor activity can lead to early detection of fictitious vendor schemes and prevent payments to fraudulent accounts. This proactive approach significantly reduces the risk of long-term fraud schemes taking root in your organization, protecting your financial resources and maintaining the integrity of your vendor relationships.
2. Invoice Anomalies
Fraudulent invoices often contain subtle discrepancies that can be detected through careful scrutiny.
Red flags to look for:
- Invoices with round number amounts
- Sequential invoice numbers from the same vendor
- Invoices just below approval thresholds
- Inconsistencies in font, format, or logo compared to legitimate invoices
How to detect:
- Implement automated invoice matching systems
- Conduct random detailed audits of invoices
- Train AP staff on common invoice fraud indicators
By diligently checking for invoice anomalies, you can substantially reduce losses from fake or inflated invoices. This attention to detail not only improves the accuracy of your payment processing but also enhances your ability to identify and investigate suspicious transactions, creating a more robust defense against invoice-related fraud.
3. Unusual Payment Patterns
Abnormal payment activities can be a sign of various types of AP fraud.
Signs to watch for:
- Multiple payments to the same vendor on the same day
- Payments made to vendors outside of normal business hours
- Sudden changes in payment methods for established vendors
- Increase in rush payment requests
How to identify:
- Use data analytics to review payment trends and anomalies
- Implement segregation of duties in payment processing
- Regularly reconcile bank statements with AP records
Staying alert to unusual payment patterns enables early detection of check tampering or ACH fraud. This vigilance helps prevent duplicate payments and improves overall cash flow management. By closely monitoring payment activities, you create a more secure and efficient accounts payable process.
4. Employee Behavior Changes
Sometimes, the behavior of employees involved in the AP process can provide clues to potential fraud.
Behavioral red flags:
- Employees who never take vacations or are overly protective of their work
- Sudden changes in an employee's lifestyle or spending habits
- Resistance to procedural changes or audits in the AP department
- Unusually close relationships with certain vendors
How to observe:
- Implement mandatory vacation policies
- Encourage a culture of open communication and whistleblowing
- Conduct regular job rotations in finance roles
Awareness of employee behavior can lead to early detection of insider fraud schemes. By fostering a culture of ethical behavior and open communication, you not only reduce the risk of long-term embezzlement but also improve the overall ethical climate of your organization, making it more resistant to various forms of internal fraud.
5. System Access Anomalies
Unusual system access patterns can indicate attempts at fraud or unauthorized changes to AP data.
Indicators to monitor:
- After-hours logins to AP systems
- Excessive password reset requests
- Unusual volume of deleted or modified records
- Access to AP systems from unexpected locations
How to track:
- Implement robust system logging and monitoring
- Use User and Entity Behavior Analytics (UEBA) tools
- Regularly review and update system access rights
Vigilance in monitoring system access can lead to early detection of cyber-based fraud attempts and prevent unauthorized system changes. This proactive approach not only protects your accounts payable process but also enhances your organization's overall cybersecurity posture, creating a more secure environment for all financial operations.
6. Discrepancies in Financial Records
Inconsistencies between different financial records can be a sign of manipulation or fraud.
Areas to examine:
- Differences between AP aging reports and general ledger balances
- Unusual journal entries affecting AP accounts
- Discrepancies between physical inventory and AP records for goods received
How to identify:
- Conduct regular reconciliations between different financial records
- Implement continuous monitoring systems for real-time detection of discrepancies
- Perform surprise audits of AP processes and records
Scrutiny of financial records enables early detection of accounting manipulation and significantly improves the accuracy of financial reporting. This vigilance enhances your ability to detect and prevent various types of AP fraud, ensuring the integrity of your financial data and supporting sound business decisions based on reliable information.
5 Ways to Prevent Accounts Payable Fraud
# 1 Implementing Strong Internal Controls
Strong internal controls are the foundation of fraud prevention in accounts payable. By establishing robust processes and checks, you can significantly reduce the risk of fraudulent activities.The core activities include:
- Segregation of duties: This involves dividing tasks among different employees to ensure no single person has complete control over a transaction. For example, the person who approves invoices should not be the same person who processes payments.
- Regular audits and reviews: This includes conducting both scheduled and surprise audits of the accounts payable process, transactions, and records to detect any irregularities or fraudulent activities.
- Approval hierarchies: This involves setting up a multi-level approval process for invoices and payments, especially for high-value transactions, to ensure proper oversight and reduce the risk of fraudulent approvals.
Best Practices:
- Clearly define roles and responsibilities within the accounts payable department.
- Implement a system of checks and balances where each step of the AP process is verified by a different individual.
- Use automated systems to enforce approval hierarchies and maintain audit trails.
- Conduct both internal and external audits regularly, including surprise audits.
- Establish clear policies for invoice approval, including dollar thresholds that require additional levels of approval.
Pro-Tip: Rotate responsibilities periodically among AP staff to prevent long-term fraudulent collaborations and provide fresh perspectives on processes.
#2 Leveraging Technology
Modern technology offers powerful tools to detect and prevent accounts payable fraud more efficiently and effectively than manual processes alone.
- Automated AP systems: These are software solutions that automate various aspects of the accounts payable process, including invoice processing, payment approvals, and record-keeping.
- Data analytics and fraud detection software: These tools analyze large volumes of transaction data to identify patterns, anomalies, or red flags that may indicate fraudulent activity.
- Artificial Intelligence and Machine Learning solutions: These advanced technologies can learn from historical data to predict and flag potential fraudulent activities, continuously improving their accuracy over time.
Best Practices:
- Implement a robust automated AP system that includes features like three-way matching and duplicate invoice detection.
- Regularly update and maintain your AP software to ensure it has the latest security features.
- Utilize data analytics tools to monitor transactions in real-time and flag suspicious activities.
- Invest in AI and ML solutions that can adapt to new fraud patterns and provide predictive insights.
- Ensure proper integration between different financial systems to maintain data consistency and enable comprehensive analysis.
Pro-Tip: Set up real-time alerts for suspicious activities, allowing for immediate investigation and intervention.
Related Article: How Fraudsters Are Exploiting AI to Conduct Illicit Activities
# 3 Employee Education and Training
Well-informed employees are your first line of defense against accounts payable fraud.
- Fraud awareness programs: These are training initiatives designed to educate employees about different types of fraud, red flags to watch for, and the importance of fraud prevention.
- Ethical business practices: This involves establishing and promoting a culture of ethical behavior within the organization, particularly in financial dealings.
- Whistleblower policies: These are procedures that allow employees to report suspected fraudulent activities confidentially and without fear of retaliation.
Best Practices:
- Conduct regular, comprehensive fraud awareness training for all employees involved in the AP process.
- Develop a clear code of ethics and ensure it's well-communicated and understood by all employees.
- Implement a confidential whistleblower hotline or reporting system.
- Regularly reinforce the importance of ethical behavior through company communications and leadership example.
- Provide ongoing education about new fraud schemes and prevention techniques.
Pro-Tip: Use real-world examples and case studies in your training to make it more engaging and relevant.
#4 Vendor Management
Proper vendor management is crucial in preventing accounts payable fraud, especially those involving external collusion.
- Thorough vetting process: This involves conducting comprehensive background checks and financial assessments of potential vendors before onboarding them.
- Regular vendor audits: This includes periodically reviewing vendor accounts, transaction histories, and performance to identify any irregularities or suspicious patterns.
- Maintaining an approved vendor list: This involves keeping a centralized, up-to-date list of vetted and approved vendors to prevent payments to fraudulent or unapproved entities.
Best Practices:
- Implement a rigorous vendor onboarding process that includes verification of business credentials, tax information, and bank details.
- Conduct regular reviews of vendor performance, pricing, and transaction history.
- Maintain a centralized, secure database of approved vendors and regularly update it.
- Implement a formal process for adding new vendors that requires multiple levels of approval.
- Use third-party verification services to validate vendor information and detect potential conflicts of interest.
Pro-Tip: Use third-party verification services to validate vendor credentials and ownership information.
#5 Continuous Monitoring and Improvement
Fraud prevention is an ongoing process that requires constant vigilance and adaptation.
- Real-time transaction monitoring: This involves continuously tracking AP transactions to quickly identify and investigate any suspicious activities.
- Regular process reviews: This includes periodically evaluating and updating AP processes to address new vulnerabilities or inefficiencies.
- Staying informed about new fraud schemes: This involves keeping up-to-date with the latest trends in AP fraud and adjusting prevention strategies accordingly.
Related Article: How to Reconcile Accounts Payable & Receivable on QuickBooks
Best Practices:
- Implement automated systems for real-time monitoring of AP transactions.
- Regularly review and update AP processes and controls to address emerging risks.
- Join industry associations or forums to stay informed about new fraud schemes and prevention techniques.
- Encourage a culture of continuous improvement where employees are motivated to identify and report process weaknesses or potential fraud risks.
- Conduct regular risk assessments to identify vulnerabilities in your AP process and address them proactively.
Pro-Tip: Encourage feedback from employees at all levels to identify potential process improvements or fraud risks.
Related Article: Fraud Risk Management Guide 2024
Conclusion
Accounts Payable fraud remains a significant threat to businesses, potentially causing substantial financial losses and reputational damage. By understanding common fraud types, recognizing red flags, and implementing robust prevention strategies your organization can significantly reduce its risk exposure. NSKT Global can be your trusted partner in this effort, offering comprehensive solutions tailored to your specific needs, including advanced AP automation systems, customized employee training programs, thorough vendor management services, regular risk assessments, and ongoing support to keep your fraud prevention strategies up-to-date. With NSKT Global's expertise, you can enhance your organization's financial security, streamline your AP processes, and focus on what matters most - growing your business.







