Table of Contents
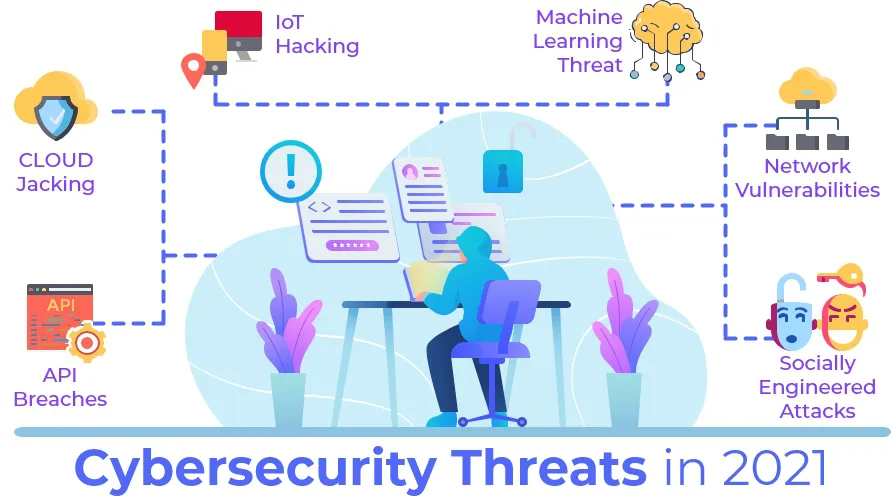
With rapidly developing technology in the present era, threats have also evolved to premier levels, such that, if not attended, can disrupt or shut the entire business down. Randomly occurring data breaches- government and private, crypto-jacking, microchip hacking are some of the newly emerged threats apart from conventional data theft, phishing, unauthorized access or intrusion, etc. There are no specified targets, every firm that pays no or less heed to cybersecurity is the potential target in the modern age. With data being the biggest valuable resource of a firm, it is most likely targeted other than finances. The best way to be safe is to be acquainted with modern threats and get partnered with a reputed cybersecurity firm. Here are some of the modern-day threats:
- Cloud Security/ Cloud Jacking: As a majority of the businesses have shifted their operations onto the cloud platforms, this is the biggest cybersecurity concern of the year and coming years. With sensitive data being stored onto cloud platforms, a slight mistake in the security of such a system could cause a disastrous amount of damage. Misconfiguration, improper security, data theft, DDoS attacks are among the major risks associated with cloud jacking or cloud security. It can be avoided by using the security services of a reputed firm that provides regular updates.
- IoT Hacking: With IoT becoming immensely popular across the globe, threats have also increased with their complexity level. The medical sector faces the biggest exposure to this risk as there are many sophisticated IoMT devices. The biggest reason being, the nascence of such devices as they have not been rolled out completely, therefore developing a cybersecurity strategy becomes a challenge.
- Network Vulnerabilities: With rolling out of 5g in many countries and 5G-to-WiFi handover, gaps in skill and sophistication of the cybersecurity can be easily exploited by the hackers. To save bandwidth, calls are switched to Wi-Fi therefore increasing the risk of a breach, due to vulnerabilities present in the system between handover.
- API Breaches: Many of the firms which readily use API for operations, don’t have robust security for the API they use, as it is given less priority than web security. As a major chunk of such firms provides external developers to modify the ecosystem or the platform to make it better, it could be heavily misused risking financial processes, messaging, and peer-to-peer social media. This could be the biggest exploitation point for cybersecurity threats.
- Machine Learning Threat: With Machine learning being implemented into every domain of the business to automate the process, hackers can exploit vulnerabilities present in them to coordinate an attack. As machine learning utilizes data from social media or crowd-source which is associated with the ratings, reviews, financials, web traffic, etc. hackers can misuse this data and pose a threat, putting the brand image at risk. AI-powered cyber threats also come under this domain. AI fuzzing which is used to trace vulnerabilities can also be compromised to launch cyber-attacks.
- Deep fake: This is a rather enhanced form of cybersecurity in which a forged video or audio for illicit purposes such as disrupting business operations, financial ambiguities, the spread of misinformation. It is one of the emerging cybersecurity threats causing a lot of trouble in the future.
- Socially Engineered Attacks: Firms and individuals often reveal their sensitive information like card or login details through engineered attacks such as phishing. This data is utilized to cause financial frauds and data thefts. This is one of the major cybersecurity risks in the past, with millions of firms getting affected by it whether knowingly or unknowingly. In the current times, Phishing is not limited to mails, but have extended to SMS, WhatsApp, and social media platforms too.
With Google being down a few days back, it is to be understood strongly that cybersecurity should be one of the key investments of the firm. Thus the need for a robust cybersecurity strategy from reputed firms like NSKT is quintessential.